NEW YORK (CNNMoney)
The attack is similar to last year's raid on South Korean banks and telecoms -- one that the country's intelligence officials attributed to the North Korean government.
Here are the latest findings from security researchers at antivirus maker Kaspersky.
Hackers destroyed data on Sony Pictures computers with the same kind of digital weapon used against South Korea.
The malware was built using Korean language -- an odd choice. Most hackers use English or Russian.
And the creepy message that popped up on Sony Pictures employees' computers has the same style -- colors, human skeletons, misspellings -- as those used against South Korea.
"Those are striking similarities," said Kaspersky researcher Kurt Baumgartner. "When you put all of that together, there's an actor that becomes more clear."
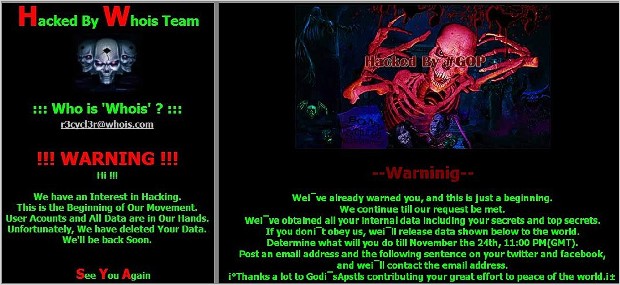 At left, the 2013 threat against South Korea. At right, the Sony hackers.
At left, the 2013 threat against South Korea. At right, the Sony hackers. There are more similarities.
The malware used against South Korea was called DarkSeoul. The one used on Sony is Destover. Security experts say it's impossible to speak of one without the other.
Both were incredibly destructive to businesses. They slipped into computers and wiped them clean.
Both types of malware were built with similar timing, customized to their specific victims two days before the attack. Other hacks might use malware created with a different lead times.
"It's a copycat," said Jaime Blasco, director of the computer security group AlienVault Lab, who analyzed the malware.
Then there's the motive. Sony is about to release "The Interview," a comedy about a plot to kill North Korean leader Kim Jong-Un. Is this retribution? Sony executives have already suspected North Korea might be the culprit, calling it "a terrorist attack."
What's more, the Sony Pictures hack has a different purpose than many recent ones. Cybercrime from China has been associated with stealing secrets from U.S. companies. Crime syndicates in Russia have focused on credit cards. "Hacktivists" disrupt companies or governments -- but claim a clear, idealistic mission.
The Sony Pictures hack was purely about destroying information and embarrassing the company. Hackers stole movie scripts, entire films, internal memos and personal information on movie stars and Sony employees. Then they wiped computers.
"That's why this one feels so different. This is about hurting Sony," said Carl Wright, formerly the chief information security officer for the U.S. Marine Corps and now general manager for TrapX Security.
Sony Pictures did not return requests for comment.
The timing couldn't have been worse. Earlier this year, Sony laid off many employees, including members of its comparatively tiny cybersecurity team, according to a former employee in that group.
Adding to the pain: Sony lost its top cybersecurity executive just before the hack. It plucked a top official from the Department of Homeland Security, Philip Reitinger, to become the company's chief information security officer after its PlayStation network was hacked in 2011 and the company lost more than $170 million. Reitinger quit to start his own company in Virginia in September, just two months before this latest hack.
Reitinger did not respond to requests for comment.
Related: Are you safe? CNNMoney's cybersecurity magazine
First Published: December 5, 2014: 9:05 PM ET
Anda sedang membaca artikel tentang
Sony hack: Signs point to North Korea
Dengan url
http://kasiatbuatsehat.blogspot.com/2014/12/sony-hack-signs-point-to-north-korea.html
Anda boleh menyebar luaskannya atau mengcopy paste-nya
Sony hack: Signs point to North Korea
namun jangan lupa untuk meletakkan link
Sony hack: Signs point to North Korea
sebagai sumbernya


0 komentar:
Posting Komentar